Article Number: 000167250
ScaleIO: CA signed certificate must be approved manually
Article Content
Symptoms
Issue Description
Message seen: "CA signed certificate must be approved manually"
Scenario
When using 3rd party certificates, we may see this message, "CA signed certificate must be approved manually"
Symptoms
When using 3rd party certificates for the MDMs, we may see this message, "CA signed certificate must be approved manually" when logging into the ScaleIO GUI: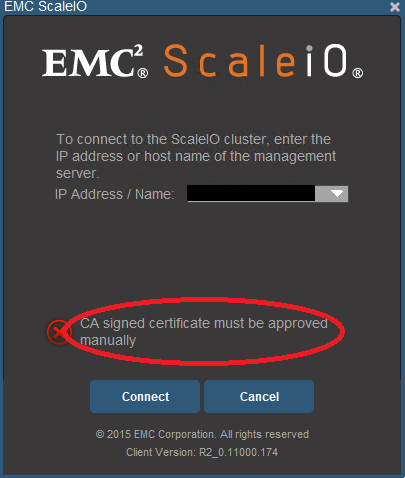
The message can also be seen when approving the MDM certificates while already logged into the GUI, but does not allow the ability to confirm the certificate:
Impact
Unable to approve the certificate for the GUI to use or log into the GUI when the certificate has not yet been approved.
Cause
Resolution
Workaround
The certificates must be added (approved) to the GUI keystore manually using keytool. Be sure that the alias is unique. ScaleIO will typically use the certificate's full subject.
You can obtain info from the certificate with this command: "openssl x509 -in [certificate file] -text -noout". While this info can be used to create the alias, it just needs to be unique.
An example command will look like this:
keytool -import -trustcacerts -alias [unique_alias] -file [path_to_the_certificate_file] -keystore [path_to_certificates_folder]/truststore.jks
keytool -import -trustcacerts -alias "givenname=mdm, ou=asd,o=emc, l=hopkinton, st=massachusetts, c=us, cn=centos-6.4-adi5" -file c:\temp\centos-6.4-adi5.cer -keystore C:\Users\Administrator\AppData\Roaming\EMC\scaleio\certificates\truststore.jks
On a Windows host, keytool will be found in C:\Program Files\Java\<JRE_Version>\bin
On a Linux host, keytool will typically be found in /usr/bin
To view the certificates that are currently in the keystore:
keytool -list -v -keystore C:\Users\Administrator\AppData\Roaming\EMC\scaleio\certificates\truststore.jks
By default, the keystore password is "changeit" (without the quotes).
*NOTE: This information can also be found in the ScaleIO 2.0.x User Guide documentation, under the section titled "Using Keytool to add certificates to external components"
Impacted versions
All ScaleIO v2.x versions
Fixed in version
Working as designed
Article Properties
Last Published Date
20 Nov 2020
Version
2
Article Type
Solution